Everyone has heard about hackathons, this is especially true for a university full of engineering students. However, not many of us have actually experienced one before. I had never participated in one until just recently. Before this, I had the common misconception that a hackathon (hack+marathon) only involves coding for an entire day, which is why I never participated (because I am terrible when it comes to coding). In fact, not all hackathons are about coding, as the main aim of the event is problem-solving. A prime example of such a hackathon was the Cypher Hack a national-level, cybersecurity hackathon conducted by the Computer Society of India at ‘Fr. Conceicao Rodrigues Institute of Technology’.
Unlike other hackathons this was a security hackathon where we had to create stuff that would be needed in the world of cybersecurity.
My first time ever attending a hackathon and that too a security hackathon the pressure, anxiety, nervousness, the excitement was REAL. My team comprised of 3 other members, 2 of whom I had never met. We met at the venue and talked about how we would tackle the problem statement. There were topics given by the people who were organizing this event. We chose our own, our problem statement was Automated Vulnerability Assessment Using a Remote Pi device. Those are some big words in the title, let me explain it to you word by word.
What is Vulnerability Assessment
Every organization is a target for hackers. The best thing a company can do is conduct an audit1. Audits are a way to detect security vulnerabilities in the system or the network of the organization with various techniques, the same techniques as that of a real-life black hat hacker aka bad guys. It focuses on identifying vulnerabilities2 in the network, server, and system infrastructure.
Adding Automated in front of it now means we are just doing it automatically by the push of a button or here in this case by the help of Pi device, Pi is just a dumbed-down version of a computer with Linux as its OS in it and it’s the size of a credit card, you plug it in devices and it works. All of this means that we were making something that was going to help companies do the security stuff faster and it’s cheap and the size of a credit card. FANTASTIC! right?
Presentation
We had to present it now in front of the judges what we were building as 3 hours had been already up. One of the judges in the panel was Venkata Satish, who has been awarded CISO3 of the year in India, so in my mind as my first impression, I had to present it as well as I could .
Break
After 5 hours or so, we had a break from our work station and in that time period, I got to interact with the remaining teams in the hackathon (I mean, you are basically stuck with everyone in the same area for the entirety of the event). There were 15 teams or so, and all of their projects were really innovative and it was inspiring to see how they were tackling their problem statements effectively. Even though everyone was busy perfecting their prototype and bringing their ideas to life throughout the event, we still managed to mingle around and meet new friends along the way.
Here’s a glimpse of what problems were given to us:
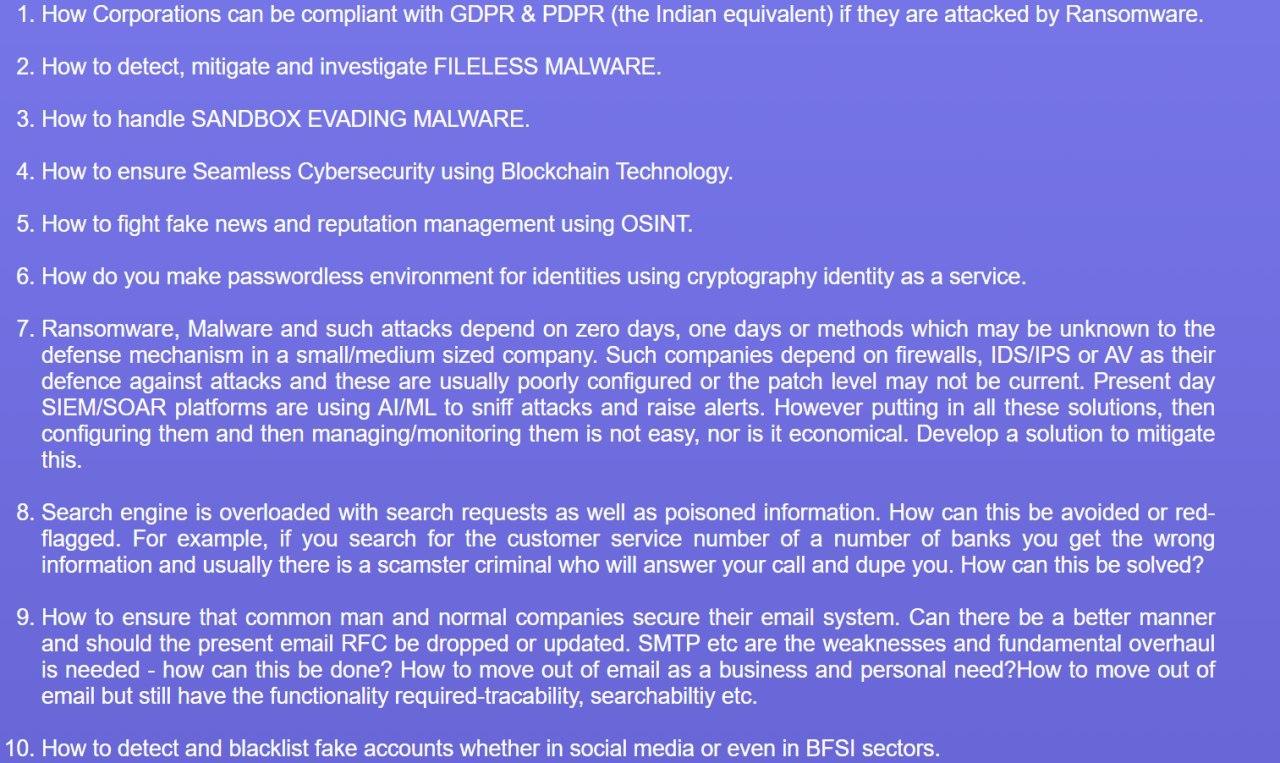
Projects made by people on Blockchain and OSINT were the most eye-catchy ones as not a lot of people use these technologies or get their hands dirty as for most of them it looks overkill.
After the break time, a couple of hours had passed our project’s hardware side had been finished, we were working on the front end side to make it more User Friendly for people to use and understand. Before the final round, professionals and experts in the fields related to hackathons and cybersecurity came as advisors. They inspected our work and asked us questions related to the same. Each of them asked us questions how it would help different scales of companies, on how a person not having a computer background can operate these devices, etc. They explained to us and cleared some of our doubts on how companies think and why they would need our product and how we need to sell it to a company and mostly to which type of companies. It was a really informative session with all of them. Not only were they able to see gaps within our idea, but they were also able to add on to what we already had.
Finals
After working for 12 hours on this project, we needed to show it to the judges, whether complete or not, we still had kinks we needed to sort in our project, it still wasn’t entirely User-Friendly. We showed the judges what we had been working on and we explained to them how they can start the Pi device remotely and conduct the VAPT audit.
After a while, all the teams were called for the announcement of winners, they gave us insight on how a team needs to perform in a hackathon such as this, what preparations should be made before and how we need to manage and gauge our time properly, how we need to present it more professionally in front of the panelists, what we can do with the product we’d made in the future and how we can work on it to make it more efficient. After this they called out the names of the teams to present them with what they had won– our team name was also called. We had secured the 1st place in the hackathon, 2 of my team members were offered Internships on the spot, and then we got a cash prize of 15K. We all agreed that the real prize was the pride and happiness we got out of winning the competition and defeating other teams.
P.S -
If you are interested and want to see the project my teammate has written a perfect blog explaining how you can program this type of product yourself, here’s the EXPLANATION – check it out. Anyway I did not explain any programming stuff we did in the project, this was just my experience, visit THIS for more coding stuff, it’s REALLY good.